Nestict.com Linktree
Forms CBC Leaving Form NPS Medical Examination Form Vendor Information Form JSS Exams Grade 7 Grade 7 Creative Arts & Sports Questions Grade 7 Christian Religious Education Questions Grade 7…
![]()
Felis consequat magnis est fames sagittis ultrices placerat sodales porttitor quisque.

Forms CBC Leaving Form NPS Medical Examination Form Vendor Information Form JSS Exams Grade 7 Grade 7 Creative Arts & Sports Questions Grade 7 Christian Religious Education Questions Grade 7…
![]()
Step 1: Preparing Your VPS Before installing Webuzo, ensure your VPS is updated and ready for installation. Log in to your VPS via SSH: Open a terminal and connect…
![]()
The Role of Proxies in IT, Cybercrime, and Economics: A Comprehensive Look Proxies, in the context of IT, are servers that act as intermediaries between end-users and the websites or…
![]()
Development, Mobile App Development, Domains & Web-Hosting Services, Bulk SMS , CCTV & Biometrics, Internet & Networking Solutions, Website Maintenance, ICT Consulting etc Find Us We Are Online 24/7 To…
![]()
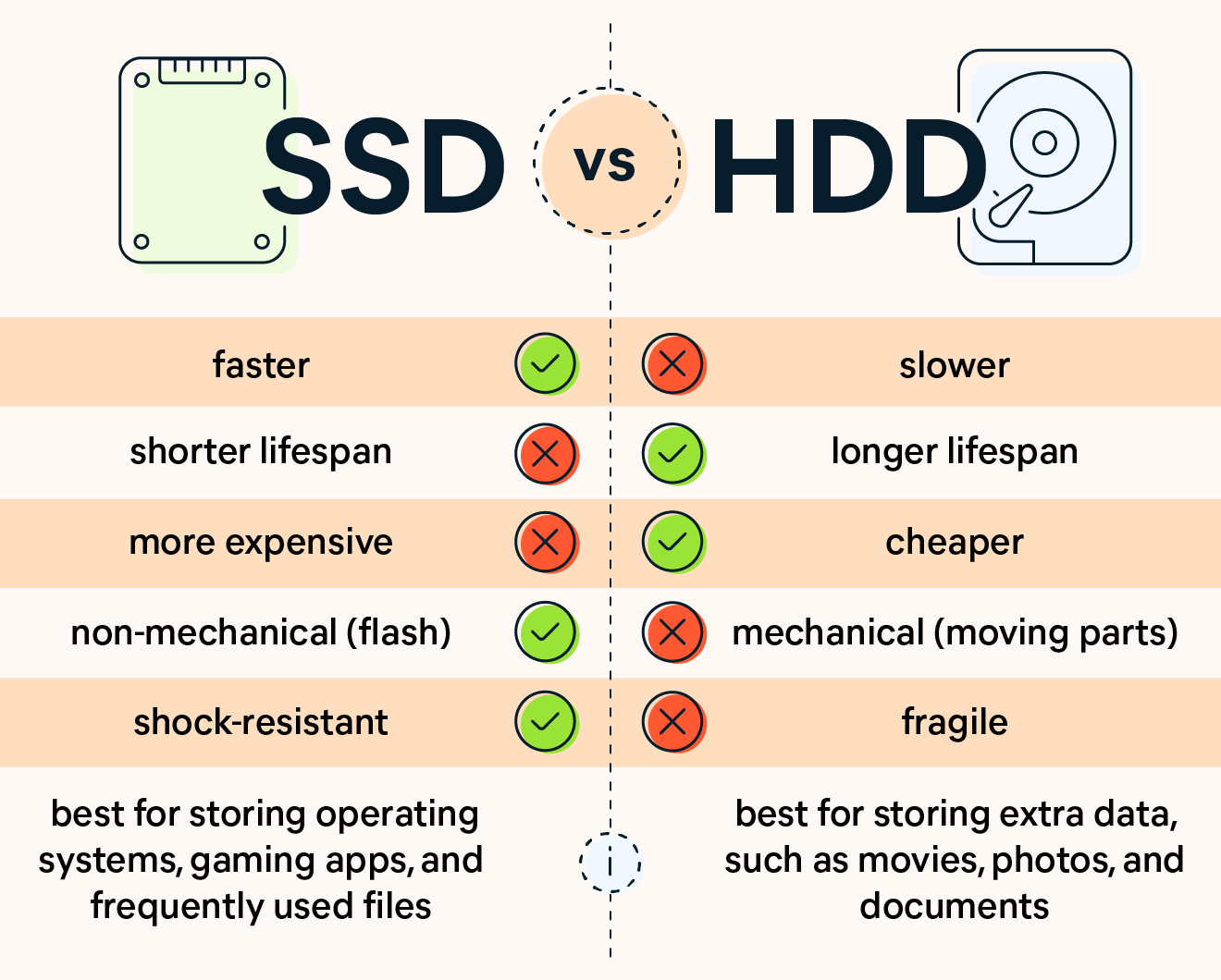
When comparing NVMe storage, SSD (SATA SSD), and HDD, each has distinct characteristics, performance levels, and ideal use cases. Here’s a breakdown of these three types of storage: 1. HDD…
![]()
Two related commands that every system administrator runs frequently are df and du. While du reports files’ and directories’ disk usage, df reports how much disk space your filesystem is using. The df command displays the amount of disk…
![]()
How to Reset Epson L382 Printer Turn on the printer and connect the USB cable Download Resetter Epson L 382 Extract file Open AdjProg-esk.exe – Accept (OK) Particular adjustment mode…
![]()
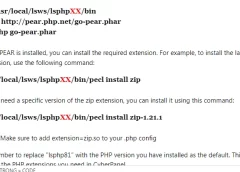
Follow below instructions for installing PHP extensions in CyberPanel for users who cannot find the desired extensions in the Server > PHP > Install Extensions section or in the LiteSpeed repository.…
![]()
FEATURES Main application/modules (all optional) Third-Parties Management: Customers, Prospects (Leads) and/or Suppliers + Contacts Members/Membership/Foundation management Product Management – Products and/or Services catalog – Stock / Warehouse management + Inventory…
![]()
DOLIBARR An all-in-one suite • Enable only the features that you want: Whatever your needs are (Customer Relationship Management, Sales, Human Resources, Logistics, Stock, Invoicing, Accounting, Manufacturing, Marketing, Foundation Management, Surveys,…
![]()





![[Assorted] Comprehensive List of Postal Codes in Kenya: From A to Z](https://www.blog.nestict.com/wp-content/uploads/2024/08/The-5-Best-Keyboards-For-Typing-Summer-2024-Reviews-RTINGS.com_.jpg)


![[Resource]: Installing Webuzo on Your Nestict Cloud VPS: A Detailed Guide](https://www.blog.nestict.com/wp-content/uploads/2024/12/image.webp)

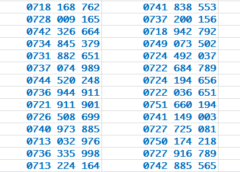
![[Resource] : Comprehensive List of Equity Bank Codes Across Kenya by Region](https://www.blog.nestict.com/wp-content/uploads/2024/12/image-5.png)


![[Continuation]: Current Challenges in Making Physics and Geography Compulsory](https://www.blog.nestict.com/wp-content/uploads/2024/12/The-universe-of-mathematics-physic-and-astronomy-its-ama…-Flickr.jpg)
![[Resource] : Why Physics and Geography Should Be Compulsory Like Mathematics in Education](https://www.blog.nestict.com/wp-content/uploads/2024/12/image.png)
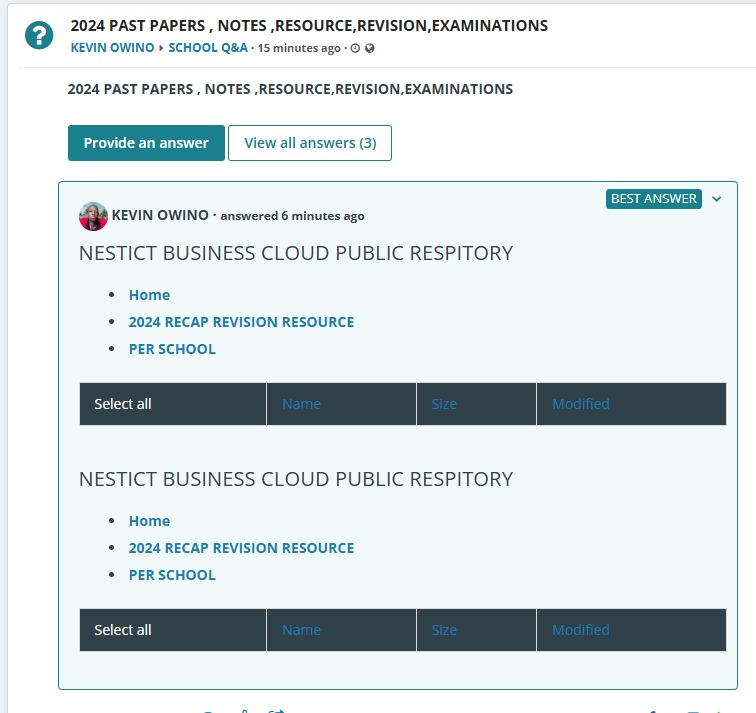
![[LINKTREE] 2024 PAST PAPERS , NOTES ,RESOURCE,REVISION,EXAMINATIONS](https://www.blog.nestict.com/wp-content/uploads/2024/10/SCHM.jpeg)


![Maritime Terms, Abbreviations and Acronyms [Shipping Terms – Searchable]](https://www.blog.nestict.com/wp-content/uploads/2024/09/Container-Stowage-Stock-Illustrations-–-71-Container-Stowage-Stock-Illustrations-Vectors-Clipart-Dreamstime.jpg)
![Maritime Terms, Abbreviations and Acronyms [ Shipping Terms]](https://www.blog.nestict.com/wp-content/uploads/2024/09/image.png)





![[Explainer]: NVMe storage, SSD (SATA SSD), and HDD](https://www.blog.nestict.com/wp-content/uploads/2024/08/Laptops-are-available-with-SSDs-and-HDDs.png)

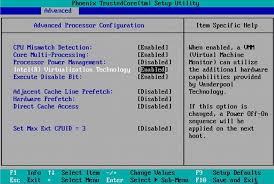





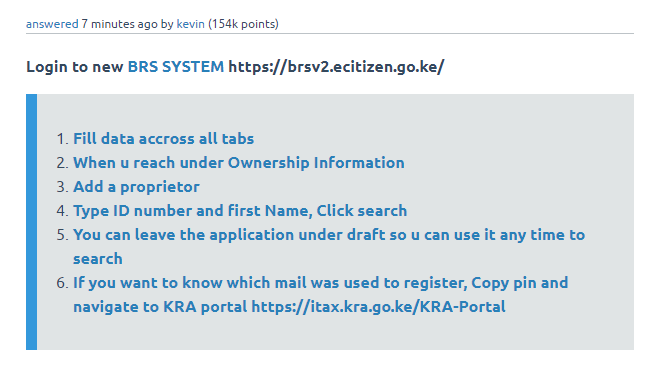
![[Updated 2024] – Passport Application FOR CHILDREN ONLY(PERSONS UNDER 18 YEARS)](https://www.blog.nestict.com/wp-content/uploads/2023/09/keppp-240x172.png)
![[Updated 2024] -Passport Application FOR ADULTS ONLY-PERSONS OVER 18 YEARS](https://www.blog.nestict.com/wp-content/uploads/2023/09/EAF-Passport-e1631045054464-400x800-1-240x172.jpg)






![[Assorted] Comprehensive List of Postal Codes in Kenya: From A to Z](https://www.blog.nestict.com/wp-content/uploads/2024/08/The-5-Best-Keyboards-For-Typing-Summer-2024-Reviews-RTINGS.com_.jpg)


![[Resource]: Installing Webuzo on Your Nestict Cloud VPS: A Detailed Guide](https://www.blog.nestict.com/wp-content/uploads/2024/12/image.webp)

![[Resource] : Comprehensive List of Equity Bank Codes Across Kenya by Region](https://www.blog.nestict.com/wp-content/uploads/2024/12/image-5.png)



![[Continuation]: Current Challenges in Making Physics and Geography Compulsory](https://www.blog.nestict.com/wp-content/uploads/2024/12/The-universe-of-mathematics-physic-and-astronomy-its-ama…-Flickr.jpg)
![[Resource] : Why Physics and Geography Should Be Compulsory Like Mathematics in Education](https://www.blog.nestict.com/wp-content/uploads/2024/12/image.png)


![[LINKTREE] 2024 PAST PAPERS , NOTES ,RESOURCE,REVISION,EXAMINATIONS](https://www.blog.nestict.com/wp-content/uploads/2024/10/SCHM.jpeg)



![Maritime Terms, Abbreviations and Acronyms [Shipping Terms – Searchable]](https://www.blog.nestict.com/wp-content/uploads/2024/09/Container-Stowage-Stock-Illustrations-–-71-Container-Stowage-Stock-Illustrations-Vectors-Clipart-Dreamstime.jpg)
![Maritime Terms, Abbreviations and Acronyms [ Shipping Terms]](https://www.blog.nestict.com/wp-content/uploads/2024/09/image.png)







![[Explainer]: NVMe storage, SSD (SATA SSD), and HDD](https://www.blog.nestict.com/wp-content/uploads/2024/08/Laptops-are-available-with-SSDs-and-HDDs.png)














![[Updated 2024] – Passport Application FOR CHILDREN ONLY(PERSONS UNDER 18 YEARS)](https://www.blog.nestict.com/wp-content/uploads/2023/09/keppp-240x172.png)
![[Updated 2024] -Passport Application FOR ADULTS ONLY-PERSONS OVER 18 YEARS](https://www.blog.nestict.com/wp-content/uploads/2023/09/EAF-Passport-e1631045054464-400x800-1-240x172.jpg)








Notifications