The Role of Proxies in IT, Cybercrime, and Economics: A Comprehensive Look
Proxies, in the context of IT, are servers that act as intermediaries between end-users and the websites or applications they access. They are essential for enhancing privacy, optimizing network performance, and securing data. However, the functionality of proxies extends into both legitimate and illegitimate use cases. Below, we’ll explore the role of proxies in IT, cybercrime, and economics, providing examples for a deeper understanding.
1. Proxies in IT: Enhancing Privacy, Security, and Performance
In the IT sector, proxies are commonly deployed for privacy and security. Companies and individuals alike use proxies to mask their IP addresses, enabling them to browse the internet anonymously and avoid being tracked. Furthermore, organizations use proxies to enhance network efficiency and security.
Examples:
- Web Browsing and Privacy: Companies like NordVPN and ProtonVPN provide proxy services to enhance user privacy by concealing IP addresses and encrypting data. This prevents unwanted tracking and shields sensitive information.
- Content Filtering: Schools and organizations use proxy servers to filter and block content. For instance, a company can restrict access to social media during work hours by routing employee traffic through a proxy that blocks specified sites.
- Load Balancing and Caching: Content delivery networks (CDNs), like Cloudflare, use proxies to optimize website performance by caching content closer to users. This minimizes latency, especially for users accessing resources from different geographical locations.
By using proxies, IT professionals can ensure security while also improving speed and optimizing resources. However, the same technology can be misused, leading us into the realm of cybercrime.
2. Proxies in Cybercrime: The Double-Edged Sword
While proxies play an integral role in legitimate cybersecurity, they are also a common tool in cybercrime. Cybercriminals often use proxies to obscure their identities, mask locations, and carry out malicious activities without getting detected. Some notorious proxy uses in cybercrime include distributed denial-of-service (DDoS) attacks, credential stuffing, and data scraping.
Examples:
- Anonymity for Hackers: Cybercriminals use proxies, particularly Tor (The Onion Router), to maintain anonymity while accessing the dark web or executing illegal activities. Tor routes users through a series of encrypted proxy servers, making it challenging to trace their origin.
- DDoS Attacks: Attackers can use proxy servers to mask IP addresses when launching DDoS attacks. Botnets, a network of infected computers controlled by cybercriminals, often employ proxies to generate traffic from diverse locations, making it harder for defenders to block the attack.
- Credential Stuffing: In credential stuffing, attackers use proxies to distribute login attempts across various IP addresses, bypassing security measures like IP blocking. For instance, in the 2020 Disney+ breach, hackers used credential stuffing, enabled by proxy networks, to access numerous accounts using previously compromised credentials.
Proxies in cybercrime highlight the ethical considerations of technology use. While proxies can protect legitimate users, they also enable illegal actions, requiring a balance between privacy and accountability.
3. Proxies in Economics: Market Research, Price Discrimination, and E-commerce
Proxies also play a crucial role in economics, where they aid in data collection, market research, and e-commerce pricing strategies. Companies frequently employ proxies for data gathering and competitive analysis, allowing them to view and analyze competitor offerings without revealing their identity.
Examples:
- Market Research and Web Scraping: Companies like Octoparse and Scrapy provide tools that use proxy networks to scrape public data from websites for market insights. For example, an airline might scrape competitor prices using proxies to identify trends and adjust its pricing.
- Dynamic Pricing: E-commerce platforms utilize proxies to tailor prices based on user location and browsing habits. For instance, if a user in a high-income area accesses an e-commerce site, they may see higher prices than a user in a lower-income area due to geo-targeted pricing. By routing traffic through proxies, companies can detect users’ geographical locations and implement price discrimination strategies.
- Ad Verification: Digital advertisers use proxies to check how ads appear across different regions. Proxy servers allow them to view localized versions of websites and confirm that ads display as intended to users in specific areas, ensuring accurate campaign delivery.
In the economic context, proxies contribute to competitive advantage and personalized marketing, enabling companies to gather data and customize pricing based on user demographics and location.
A proxy person is an individual who acts on behalf of another, often serving as a stand-in or representative. In various contexts, this means that the proxy person performs actions, makes decisions, or holds assets for someone else’s benefit while concealing the true party’s involvement or interests. The person using the proxy usually does so to remain anonymous, reduce risks, or circumvent legal, social, or regulatory restrictions.
In the context of crime, business, or financial transactions, a proxy person may be involved in obscuring the true ownership or source of funds, sometimes as part of money laundering or other fraudulent activities.
What Does “Proceeds Gained Through Proxy” Mean?
The term proceeds gained through proxy refers to profits, earnings, or assets obtained by a person or entity through the actions of a proxy. In simpler terms, it means that the real beneficiary of these proceeds is hidden, with the proxy serving as a front. This often occurs when the true party wants to conceal their involvement for reasons that may include privacy, avoiding legal scrutiny, or evading taxes.
Examples:
- Money Laundering: Criminals might use a proxy person to manage bank accounts or real estate investments. Any profits or assets (“proceeds”) from these activities appear to belong to the proxy but are ultimately controlled by the actual party behind the scenes.
- Political Contributions: In some cases, individuals might use proxies to contribute to political campaigns anonymously or to bypass contribution limits.
- Business Ownership: A business owner might register a company under someone else’s name (a proxy person) to sidestep legal or tax implications, but they still control the company and enjoy its profits.
14 total views , 1 views today









![[Resource]: Installing Webuzo on Your Nestict Cloud VPS: A Detailed Guide](https://www.blog.nestict.com/wp-content/uploads/2024/12/image.webp)
![[Resource] : Comprehensive List of Equity Bank Codes Across Kenya by Region](https://www.blog.nestict.com/wp-content/uploads/2024/12/image-5.png)


![[Continuation]: Current Challenges in Making Physics and Geography Compulsory](https://www.blog.nestict.com/wp-content/uploads/2024/12/The-universe-of-mathematics-physic-and-astronomy-its-ama…-Flickr.jpg)
![[Resource] : Why Physics and Geography Should Be Compulsory Like Mathematics in Education](https://www.blog.nestict.com/wp-content/uploads/2024/12/image.png)
![[LINKTREE] 2024 PAST PAPERS , NOTES ,RESOURCE,REVISION,EXAMINATIONS](https://www.blog.nestict.com/wp-content/uploads/2024/10/SCHM.jpeg)


![Maritime Terms, Abbreviations and Acronyms [Shipping Terms – Searchable]](https://www.blog.nestict.com/wp-content/uploads/2024/09/Container-Stowage-Stock-Illustrations-–-71-Container-Stowage-Stock-Illustrations-Vectors-Clipart-Dreamstime.jpg)
![Maritime Terms, Abbreviations and Acronyms [ Shipping Terms]](https://www.blog.nestict.com/wp-content/uploads/2024/09/image.png)




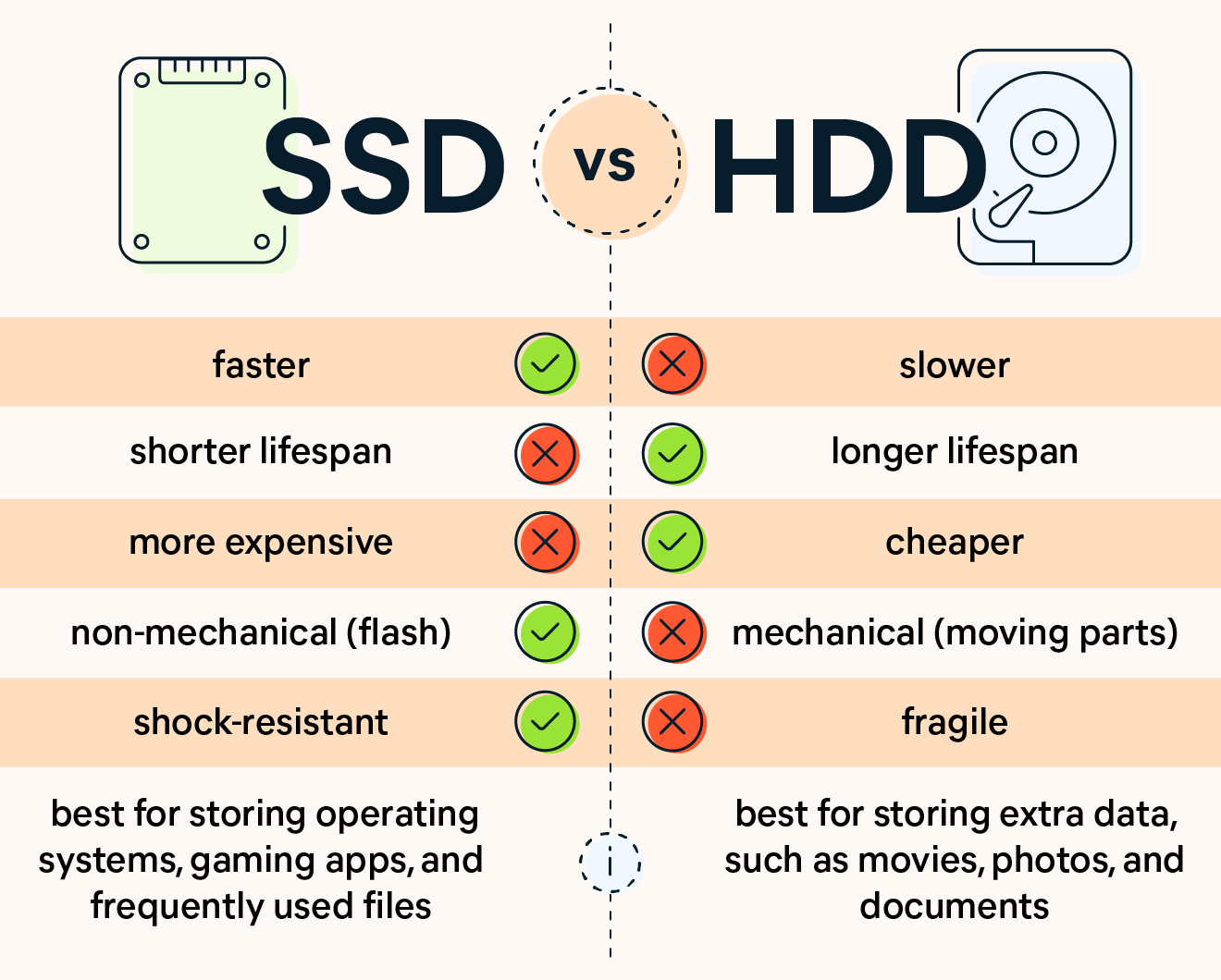
![[Explainer]: NVMe storage, SSD (SATA SSD), and HDD](https://www.blog.nestict.com/wp-content/uploads/2024/08/Laptops-are-available-with-SSDs-and-HDDs.png)





![[Updated 2024] – Passport Application FOR CHILDREN ONLY(PERSONS UNDER 18 YEARS)](https://www.blog.nestict.com/wp-content/uploads/2023/09/keppp-240x172.png)
![[Updated 2024] -Passport Application FOR ADULTS ONLY-PERSONS OVER 18 YEARS](https://www.blog.nestict.com/wp-content/uploads/2023/09/EAF-Passport-e1631045054464-400x800-1-240x172.jpg)